Assassin's Maces (杀手锏, Shashoujian)

Overview
Assassin's Mace (杀手锏, pronounced "sha-shou-jian") represents China's asymmetric warfare strategy aimed at defeating a technologically superior adversary by targeting critical vulnerabilities. Rooted in ancient Chinese strategic thinking, this concept envisions a suite of unconventional weapons and tactics designed to create devastating effects against Western military and civilian infrastructure at precisely the right moment.
The term originates from Chinese folklore, where a concealed hand mace could deliver a decisive blow against a more powerful opponent. As Michael Pillsbury notes in "The Hundred-Year Marathon," the strategy involves developing capabilities incrementally, "so that by the time the capabilities are achieved, it would be too late for the U.S. to respond." The concept gained formal recognition when President Jiang Zemin referenced shashoujian at the 16th Chinese Communist Party Congress in 2002.
These weapons operate within China's "Unrestricted Warfare" doctrine, described by PLA Colonels Qiao Liang and Wang Xiangsui, who argued that "the battlefield will be everywhere" and "all the boundaries lying between the two worlds of war and non-war, of military and non-military, will be totally destroyed." Most concerning is how these weapons could be deployed together at the "Moment of Shi" (势/勢) – the optimal strategic timing – creating cascading failures across military and civilian domains that exceed the sum of their individual effects.
Known Maces
Tactical Directed Energy Weapon (Cloud Eraser)
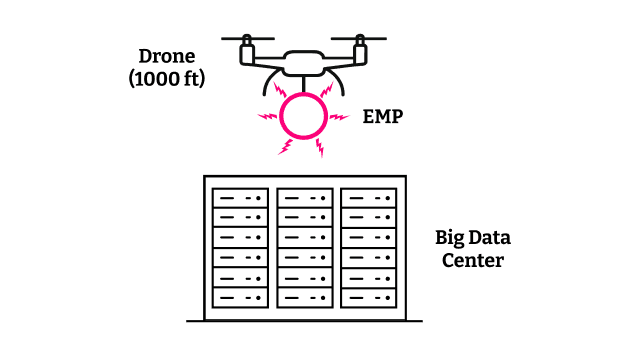
While space nukes still deliver the best line-of-sight blast radius, the practical attacker prefers a modern tactical electromagnetic pulse. Drone-mounted, and capable of delivering over 250 kV/m², Cloud Eraser hovers silently a thousand feet over your trusty data center. One hundred distributed Cloud Erasers working together from a central command can wipe out most of what we call “the cloud.”
A 2020 military report revealed China has developed a "high-powered magnetic pulse compressor" capable of generating pulses that can damage sensitive electronics. These mobile, non-nuclear EMP generators provide precision strike capability against digital infrastructure without triggering nuclear response protocols.
Power: Precise neutralization of digital infrastructure
Damage: Eliminate cloud computing capabilities
Deep Cutter (Undersea Fiber Cable Cutting Device)
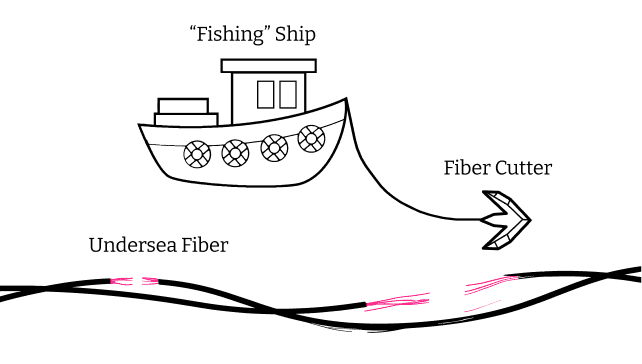
China's patented undersea cable cutting device fishes for backbone fiber. The device mounts to any vessel including "fishing ships." No fiber is too deep. Believed to be equipped on thousands of vessels worldwide, this clever cleaver is designed to "upset the world order" (their words). Operating in concert from central command, Deep Cutter could stop off 90% of global internet traffic in its tracks.
A 2020 patent application from Lishui University described a "dragging type submarine cable cutting device" designed to hook and sever undersea cables. The system allows a tugboat to drag the device along the ocean floor to cut cables without precise positioning. More recently, China revealed a powerful cable-cutting device capable of operating at depths up to 4,000 meters, developed by the China Ship Scientific Research Centre.
Power: Sever critical digital infrastructure
Damage: Turn off the rest of the world's internet
Kessler Cascade via Hyperfragmentation LEO Strike
America owns most of the world's 10,000+ Low Earth Orbit Satellites. China owns next to none. The crown jewel of asymmetric attacks, Constellation Killer lies in wait for the moment of Shi signal from Beijing. With one hyperfragmentation kinetic strike to a single LEO comes the desired result: the dreaded Kessler Cascade. Within minutes, LEO internet begins to falter. Within days, LEO internet no longer exists.
China's most notable anti-satellite test occurred on January 11, 2007, when it destroyed the Fengyun-1C weather satellite at 865km altitude, creating over 3,000 pieces of trackable debris. This single test demonstrated China's ability to trigger the Kessler Syndrome—a cascade of collisions that could render portions of orbital space unusable for all nations. The SC-19 (based on a modified DF-21 missile), DN-2, and DN-3 anti-satellite systems form the backbone of this capability.
Power: Trigger the Kessler Cascade
Damage: Eliminate LEO internet
High-Altitude Electromagnetic Pulse (HEMP)
This legacy Assassin's Mace delivers the most bang for the buck. A single strategic warhead detonated in the upper atmosphere wreaks havoc on electrical systems across thousands of square miles. Long misunderstood as the only means of achieving devastating EMPs, this Assassin's Mace has been replaced by Cloud Eraser. Why trigger Mutually Assured Destruction when you can just knock out the hundred largest data centers powering "the cloud"?
Chinese military publications specifically reference "super-EMPs" that generate peak fields of approximately 200,000 volts per meter—sufficient to damage even hardened military electronics. What makes this threat particularly concerning is that China now categorizes HEMP attacks as an extension of information/cyber warfare rather than nuclear warfare—suggesting a lower threshold for use in conflict.
Power: Disrupt, disable or destroy America's energy grid
Damage: Collapse of civil society within days
AI Prime (Artificial Intelligence Supremacy)
Second in Artificial Intelligence only to the United States of America, China's AI capabilities rest on top of extraordinarily resilient digital infrastructure. While America leads the world in AI models, China has the upper hand for two reasons: 1) Fed by Cyber Attack, Chinese AI trains on vastly superior data. 2) Assassin's Maces will degrade, disable, and destroy most of the West's software capabilities in a single day. In the subsequent AI-dependent hot war, who will emerge the victor?
China is integrating AI across multiple military domains, including the Caihong ("Rainbow") family of high-altitude UAVs, the WZ-8 stealth reconnaissance UAV, and the FH-97A "loyal wingman" drone system. Reports from 2024 reference an experimental generative AI capable of commanding drones equipped with electronic warfare weapons, significantly enhancing China's ability to coordinate complex operations in degraded information environments.
Power: Superintelligent Warfare
Damage: Absolute Control
Algorithmic Cognitive Warfare
A leaked military doctrine titled "The Future of the Concept of Military Supremacy" outlines China's ambition to map and influence the American mind. Published shortly before the first TikTok dance trend went viral, the report opens with a chilling line: "War has started to shift from the pursuit of destroying bodies to paralyzing and controlling the opponent." While American youth are nudged toward dopamine loops and digital decay, their Chinese counterparts are guided toward discipline, academic achievement, and national pride. At the same time, China's influence campaigns quietly harvest vast troves of personal and biometric data from U.S. users to convert entertainment into intelligence.
The People's Liberation Army describes cognitive domain operations as attempting to use an "invisible hand" to control opponents' will, making adversaries feel "I can't," "I dare not," and ultimately "I don't want to." Security experts have specifically cited TikTok as a potential vector for algorithmic warfare, noting the platform's extensive data collection from approximately 170 million American users and the fact that ByteDance remains legally required to assist Chinese government intelligence gathering under the 2017 National Intelligence Law.
Power: Manipulate perception and decision-making
Damage: Erode strategic will to resist
Conventional Cyber Warfare
The oldest of the digital Assassin's Maces, don't sleep on Cyber Attack. The most secure networks on the planet still rely heavily on Chinese-made boards, chips, and switches. Millions of network devices run ancient firmware instructions inspired by Sun Tzu: “Let your plans be dark and impenetrable as night, and when you move, fall like a thunderbolt.”
China has developed sophisticated conceptions of "systems destruction warfare" that target networks and systems providing U.S. forces with their technological advantage rather than engaging in symmetric warfare. By targeting command, control, and communications infrastructure before conventional operations begin, China aims to blind, deafen, and isolate adversaries through attacks on supporting digital systems.
Power: Omniscience for AI Prime
Damage: Turn the battlefield upside down
Blended Domains (Omnipresent Battlefield)
The most tragic Assassin's Mace starts from China's principle to ignore any distinction between Ba's civilians and her defenders. By erasing traditional boundaries between civilian life and war, People's Liberation Army employs social, economic, chemical, information and biowarfare before and during war. From limitless fentanyl precursors to mind-altering algorithms to destabilizing Western markets, Blended Domains before war begins pales in comparison to what happens when the Moment of Shi arrives.
This approach directly implements the "cocktail warfare" strategy advocated in "Unrestricted Warfare," which argued that “the great masters of warfare techniques during the 21st century will be those who employ innovative methods to recombine various capabilities so as to attain tactical, campaign and strategic goals.”
Power: Limitless war beyond boundaries
Damage: Schools, Libraries, Towns, Hospitals, Farms
Sources Cited
Books and Major Publications
Liang, Qiao, and Wang Xiangsui. Unrestricted Warfare: China's Master Plan to Destroy America. Echo Point Books & Media, 2015. Originally published as "超限战" by the PLA Literature and Arts Publishing House, Beijing, 1999.
Pillsbury, Michael. The Hundred-Year Marathon: China's Secret Strategy to Replace America as the Global Superpower. New York: Henry Holt and Co., 2015.
Department of Defense. Military and Security Developments Involving the People's Republic of China. Annual Report to Congress, 2022.
Academic and Research Papers
Johnston, Alastair Iain. "Shashoujian: A Strategic Revelation or Simply an Idiom?" ResearchGate, 2002.
Gabrielson, Mark. "Shashoujian: A Strategic Revelation or Simply an Idiom?" The RUSI Journal, Vol. 164, No. 3, 2019. https://www.tandfonline.com/doi/full/10.1080/03071847.2019.1643257
Elsa B. Kania. "Chinese Military Innovation in Artificial Intelligence." Center for a New American Security, June 2019.
Journals and Articles
The New Atlantis. "The Assassin's Mace." https://www.thenewatlantis.com/publications/the-assassins-mace
Farahany, Nita. "TikTok is part of China's cognitive warfare campaign." The Guardian, March 25, 2023. https://www.theguardian.com/commentisfree/2023/mar/25/tiktok-china-cognitive-warfare-us-ban
Bryen, Stephen. "China, Russia Building Super-EMP Bombs for 'Blackout Warfare'." Asia Times, May 24, 2019.
Danzig, Jason. "China's High-Altitude Electromagnetic Pulse Weapons: A Threat to US Cybersecurity and Nuclear Deterrence." The Henry M. Jackson School of International Studies, University of Washington, 2022. https://jsis.washington.edu/news/chinas-high-altitude-electromagnetic-pulse-weapons-cyberwarfare-and-nuclear-deterrence/
Government and Military Sources
MITRE Corporation. "Demystifying Shashoujian: China's 'Assassin's Mace' Concept." 2018. https://www.mitre.org/news-insights/publication/demystifying-shashoujian-chinas-assassins-mace-concept
Jamestown Foundation. "The 'Algorithm Game' and Its Implications for Chinese War Control." China Brief, Volume 21, Issue 14, July 2021. https://jamestown.org/program/the-algorithm-game-and-its-implications-for-chinese-war-control/
Jamestown Foundation. "Cognitive Domain Operations: The PLA's New Holistic Concept for Influence Operations." China Brief, Volume 21, Issue 12, June 2021. https://jamestown.org/program/cognitive-domain-operations-the-plas-new-holistic-concept-for-influence-operations/
CNA. "The PLA and Intelligent Warfare: A Preliminary Analysis." October 2021. https://www.cna.org/reports/2021/10/the-pla-and-intelligent-warfare-preliminary-analysis
Cenjows. "China's Algorithmic Warfare: Strategic Implications of AI-Driven Military Operations." 2023. https://cenjows.in/chinas-algorithmic-warfare-strategic-implications-of-ai-driven-military-operations/
Technical and Patent Resources
China Ship Scientific Research Centre. “Deep-sea Cable Cutting Device Technical Specifications.” Patent Publication, 2023.
Lishui University. "Dragging Type Submarine Cable Cutting Device." Patent Application, 2020.
CETC International Co. "Microwave Active Denial System Technical Overview." 2023.
News Sources
South China Morning Post. "China unveils a powerful deep-sea cable cutter that could reset the world order." 2023. https://www.scmp.com/news/china/science/article/3303246/china-unveils-powerful-deep-sea-cable-cutter-could-reset-world-order
Washington Times. "Inside the Ring: China advances EMP weapons, military writings reveal." September 6, 2023. https://www.washingtontimes.com/news/2023/sep/6/inside-ring-china-advances-emp-weapons-military-wr/
SpaceNews. "Pentagon report: China amassing arsenal of anti-satellite weapons." 2023. https://spacenews.com/pentagon-report-china-amassing-arsenal-of-anti-satellite-weapons/
Newsweek. "Exclusive—Chinese Patents Reveal Aim to Cut Undersea Cables." 2023. https://www.newsweek.com/china-conflict-undersea-cables-cutting-internet-data-subsea-marine-baltic-taiwan-2012396
Critical Infrastructure Terms
A
B
C
D
E
F
G
I
L
M
P
R
S
T
U
Y